LockBit persists as the most prominent Ransomware-as-a-Service (RaaS) groups in 2022, showcasing heightened capabilities in their LockBit 3.0 iteration and a persistent nature to continuously evolve.
Clik here to view.

As the LockBit RaaS group re-emerges with their new and improved ransomware, LockBit 3.0 (also known as LockBit Black), we observed new capabilities and a heightened sophistication based on their increased frequency of attack and speed to impact, posing an ever-growing threat to organisations worldwide.
PwC’s Dark Lab observed over 860 breaches between 1 October 2021 and 31 October 2022 attributed to the LockBit RaaS group. 19% of global LockBit incidents impacted the Asia Pacific (APAC) region, with industries most prominently targeted in the region being Professional Services and Manufacturing Services, comprising 44% of total incidents observed in APAC. Despite this, we assess they are still opportunistic by nature and these statistics reflect that potentially certain industries are more likely victims potentially due to their overall lower maturity of controls when compared to regulated industries.
Clik here to view.

Clik here to view.

Comprising approximately 40% of all ransomware attacks against APAC observed between 1 October 2021 and 31 October 2022, LockBit presents a persistent threat to the region. This blog extends from our previous blogs covering LockBit 2.0 to focus on the new 3.0 iteration, highlighting novel tactics, techniques, and procedures (TTPs) observed in Dark Lab’s recent incident. [1] [2]
A Recent Encounter with LockBit 3.0
In Q3 2022, PwC’s Dark Lab responded and contained a ransomware attack against a Chinese multinational conglomerate. Attributed to the LockBit 3.0 RaaS group, this was concluded with high confidence based on a number of key indicators, aligning with LockBit’s typical attack vector.
Firstly, similar to previous LockBit 2.0 incidents observed by PwC’s Dark Lab, the vulnerability exploited to obtain valid credentials was a SSL VPN vulnerability. In this instance, CVE-2018-13379 was exploited – a vulnerability in Fortinet’s outdated FortiOS and FortiProxy versions whereby an authenticated attacker may exploit the SSL VPN web portal to download system files using custom HTTP requests. [3]
Secondly, PwC’s Dark Lab discovered the presence of the LockBit executable file .lockbit and the StealBit.exe information stealer tool in the compromised environment, both of which are commonly deployed malwares by the LockBit RaaS group. [4]
| Filename | LockBit.exe |
| MD5 | ad2918181f609861ccb7bda8ebcb10e5 |
| File Type | Win32 EXE |
| File Size | 163,328 bytes |
| Filename | Stealbit.exe |
| MD5 | 72e3efc9f6c7e36a7fb498ab4b9814ac |
| File Type | Win32 EXE |
| File Size | 441,856 bytes |
StealBit.exe is a versatile, configurable information stealer with observed customisable configurations including the ability to specify network limit, maximum file size, filtering of files by keywords and file extensions, and optional features such as self-deletion and ScanShares.
A notable observation of the StealBit.exe running process was the list of keywords to filter and identify files for exfiltration, including keywords used to target files relating to specified insurance companies. Dark Lab hypothesises StealBit.exe was used to target information on the victim organisation’s insurance policy to understand their coverage pertaining to data breaches and ransomware attacks and adapt their ransom price accordingly. We posit this is a means of increasing the likelihood of their demanded ransom payment by targeting the victim’s insurance coverage, meaning that ransom payment would be covered by the insurance company, rather than the victim itself. Further, we observe keywords such as ‘violation’, ‘tax’, ‘evasion’, likely to collect evidence of the targeted victim’s misconduct to use as blackmail in the event the victim refuses to pay the ransom.
In examining the encryption process of lockbit.exe, we observed the total encryption speed of 3.8 minutes for 3,957 files (total file size 3080.16 mega byes), approximating an encryption speed of 13.6 megabytes per second. This comparatively fast encryption speed shows heightened capability of the LockBit ransomware, observed by various security researchers to have the highest encryption speed across ransomwares. [5]
Thirdly, Dark Lab observed a notable differentiator in comparison with previous LockBit 2.0 encounters – the presence of legacy RaaS group, BlackMatter’s code embedded in the LockBit codebase, signifying that the LockBit 3.0 iteration was executed in this incident. BlackMatter is a notorious RaaS group active from July 2021 to October 2021 known for targeting the U.S. health sector and suspected to be a rebranding of the DarkSide RaaS group. [6]
As observed by security researchers in the wake of LockBit 3.0, the new iteration of LockBit appears to borrow code from the legacy group with notable new features adopted from BlackMatter. This was further validated in an interview with the alleged LockBit founder, confirming that in preparation of LockBit 3.0, the group purchased the BlackMatter source code to enhance the ransomware. [7] Features utilised from the BlackMatter source code include API harvesting for privileged escalation, self-deletion of shadow copies using WMI via COM objects and the elimination of pre-existing bugs. [8]
Further investigation into the lockbit.exe executable file confirmed traces to LockBit 3.0. As evidenced below, the malware is a known malicious file matching YARA rules pinpointing relations to LockBit and BlackMatter respectively.
Clik here to view.

Clik here to view.
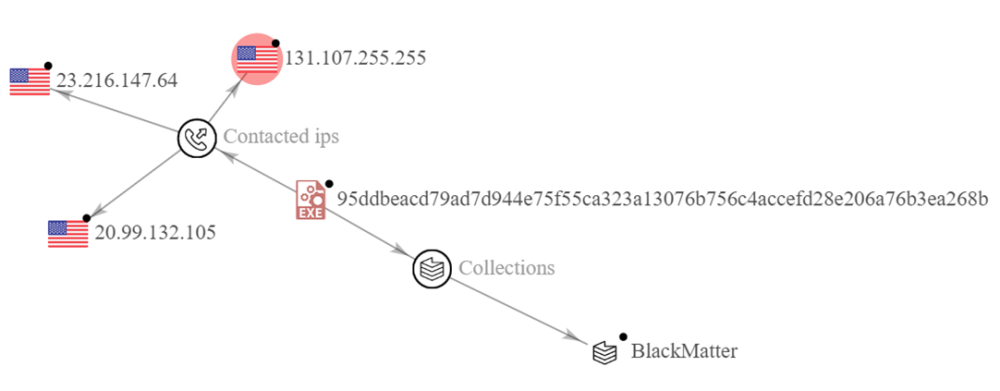
95ddbeacd79ad7d944e75f55ca323a13076b756c4accefd28e206a76b3ea268b” and confirmed association with BlackMatterThe Future of LockBit
The LockBit RaaS group has proven persistence and no means of halting operations. This is observed in the first-ever ransomware bug bounty program launched by the group in June 2022, awarding up to US$1 million to anyone able to identify critical bugs or provide innovative ideas to enhance their LockBit 3.0 ransomware. This not only exemplifies their financial viability, but it implies their intention to continue enhancing their offerings as a means of providing high consumer confidence and to retain and grow their affiliate base.
Clik here to view.

Clik here to view.

LockBit is recognised as a leader in the RaaS landscape, offering one of the best affiliate recruitment programs. This is largely due to their unique payment structure which favours affiliates and their lack of political association. [9] In an interview with an alleged LockBit member held in July 2022, the LockBit representative accredits their successful affiliate recruitment program to their emphasis on “honesty”, priding themselves as the only affiliate group known to “not touch the ransoms obtained by partners”. [10]
In a more recent interview on 30 October 2022, the blog vx-underground [11] spoke with the alleged founder of LockBit on the affiliate payment structure and origin story of the group. It was confirmed that LockBit’s founding members gain a 20% cut of affiliates’ profits, with this increasing to 30-50% in the event that the affiliate requires additional support from the group in performing negotiations with the targeted victim. The representative further confirmed that LockBit currently comprises of 10 core members (including pen testers, money launderers, testers, and negotiators) and an affiliate base of over 100 affiliates – which they aspire to grow to 300.
As observed in both interviews, LockBit has secured themselves as a market leader in the RaaS landscape due to their favourable payment structure, strong affiliate support system, and neutral political stance. As implied in the latest interview, the group endeavours to continue expanding their affiliate base which will reflect in a continuous enhancing of their ransomware products to differentiate themselves amongst other RaaS operators to attract new joiners. We posit that the RaaS scene will continue to expand as the competitive landscape will drive more effective, enticing ransomware packages – increasing accessibility and scale of operations for financially-driven low skill-levelled hackers – complete with instructions, toolkits, and custom malware to execute large-scale attacks.
Notably, LockBit affiliates are known to re-use known initial access points (e.g. SSL VPN vulnerabilities – Citrix Gateway (CVE-2019-19781), Pulse Secure (CVE-2019-11510), Fortinet FortiOS (CVE-2018-13379)). However, as per our post on LockBit 2.0’s SonicWall exploit to bypass multi-factor authentication (MFA) [12], the group is not averse to deviating from their usual attack path as we observed the affiliate chain a known SQLi vulnerability (CVE-2019-7481 or CVE-2021-20028) with an undisclosed zero-day vulnerability to circumvent the MFA access control of the victim’s SonicWall SRA SSL VPN.
A further evolution in LockBit’s attack path is their announcement to begin executing triple extortion tactics. This is in retaliation of the incident with security company Entrust, in which LockBit’s corporate data leak site was targeted by a Distributed Denial of Service (DDoS) allegedly executed by Entrust to stop Lockbit from leaking Entrust’s compromised data. This prompted LockBit RaaS to announce they will add a third extortion tactic, for maximum impact on targeted victims.
Clik here to view.

Conclusion
LockBit 3.0 affiliates work on behalf of the LockBit group to conduct ransomware campaigns against organisations and industries across the globe. As previously posited in our technical analysis of LockBit 2.0 [13], the RaaS group is financially-driven and through these incidents we observed, affiliates with a diversified capability and skillset exploit are observed to exploit SSL VPN vulnerabilities to circumvent the MFA access control and obtain initial access. Organisations are encouraged to review the TTPs leveraged by LockBit affiliates as a result of our recent incident response experience to improve their preventive and detective controls.
Check out our previous LockBit blogs for the full technical analysis:
- LockBit 2.0 affiliate’s new SonicWall exploit bypasses MFA [14]
- Technical analysis of LockBit 2.0 affiliates’ SonicWall exploit that bypasses MFA [15]
Recommendations
As RaaS groups continuously persist and evolve their attack vectors, it is vital that organisations implement robust, layered defence strategies based on the concept of zero trust.
Preventative
- Enforce a layered defence strategy incorporating secure network security protocols (including but not limited to firewall, proxy filtering, intrusion detection systems (IDS), intrusion prevention systems (IPS), secure VPNs and security gateways).
- Optimising security application configurations for effective coverage, tailoring rules and configurations to business needs, or ensuring that out-of-the-box (OOTB) configurations provide adequate coverage.
- Update your blacklist with the indicators of compromise (IoCs) shared below and block outgoing network connections to the identified C2 server. We encourage you to visit our previous LockBit blogs for an expansive list of LockBit IoCs identified by PwC’s Dark Lab.
- Disable unused administrative ports internally, such as Remote Desktop Protocol (RDP).
Detective
- Identify, detect, and investigate abnormal activity and potential traversal of the threat actor across the network, such as ensuring coverage of Endpoint Detection and Response (EDR) tools on critical endpoints, including workstations, laptops and servers.
- Regularly scan your network environment for potential vulnerability(s) exposure and remediate immediately, such as deploying available patches, establishing regular schedules updates and periodically reviewing configuration settings for potential misconfigurations.
- Conduct a search of historical logs to detect for any potential presence in your network environment, ensuring that an alert system is established should any indicators be identified. If any indicators are discovered, it is advised that a digital forensic investigation is conducted to identify the potentially foregone impact, including the compromised information and systems, and apply the appropriate containment and remediation measures.
Indicators of Compromise (IoCs)
We include the observed IoCs in our encounter with LockBit 3.0.
| Indicator | File Type |
162[.]214[.]152 [.]179 | External server of StealBit |
72e3efc9f6c7e36a7fb498ab4b9814ac | Stealbit.exe |
ad2918181f609861ccb7bda8ebcb10e5 | Lockbit.exe |
131[.]107[.]255[.]255 | IP Address |
23[.]216[.]147[.]64 | IP Address |
20[.]99[.]132[.]105 | IP Address |
Feel free to contact us at [darklab dot cti at hk dot pwc dot com] for any further information.